1) Select an image
2) Convert it into .ico (128 X 128) format using softwares like ToyCon or goto converticon.com
3) Save the image as gimp.ico into the folder whose icon you want to change.You can save the image using any name. Here, I am saving it as gimp.ico
4) Then in that drive create a text document and write the following into it
[AutoRun]
ICON=gimp.ico
5) Save it as autorun.inf
6) Then restart your computer, and wohooo... look..icon changed
SCREENSHOTS-
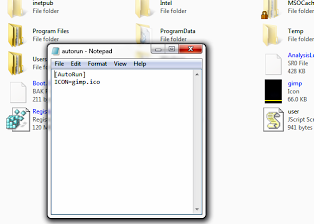 |
| 1. INF file along with image file saved in drive C. |
 |
| 2. Changes Done |